Thoughts on Getting the OSCP
Gang Gang

It has been a long while since I posted. During this time, I spent time working toward my OSCP certification. I knew that the OSCP is a certification with a reputation for being difficult. The company behind OSCP, the same company who created Kali Linux, believed in a “Try Harder” mentality when it comes to penetration testing. They believe that a successful ethical hacker is one that knows when not to give up and does everything in their power to make their exploit work. Average script kiddies may give up the moment their exploit script doesn’t pop a shell for them, while professional ethical hackers will try to diagnose the issue and see if the script is not working properly, or if there is a firewall that prevents a shell from poping up. Parts of it depends on one’s skills, but a more important portion depends on one’s grit to push through.
This philosophy of “Try Harder” also reflects in the exam format. The exam consist of 6 machines, three in an Active Directory network, and another three standalone boxes. Students are given 24 hours to hack into these machines with the objective of obtaining 70 points at least by submitting hashes on the machines. The three machines in the Active Directory contains System hashes that gives you 10, 10, and 20 points respectively, and the standalone machines has a 10 points initial access user hash and a 10 points root hash. Then after the 24 hours of exam, the students are then required to turn in a report detailing their findings. Students has to provide the commands they ran, screenshots as proof of compromise, and recommendations for mitigation. Overall the OSCP exam is not only a test on the testtaker’s skills at penetration testing and reporting, but also a test on their will to keep pushing beyond their perceived limits.
I will now tell you about the process I took to pass the OSCP. Hopefully this article will be helpful to those attempting the exam or thinking about doing so.
Pre-req: eJPT/PEH

eJPT is a good stepping stone for obtaining the OSCP. Even you don’t learn about a whole lot of techniques in the certification, as I mentioned in my review of the eJPT, it teaches you the pentest methodology of gathering information and finding vulnerabilities, exploiting and gaining initial foothold, escalating privilege, maintaining existing access, and repeat. The training material really beats this framework into your head.
As an alternative, you can also take a look at The Cyber Mentor’s Practical Ethical Hacking (PEH) course. It is much affordable, and the first half of the course is available on YouTube for Free. As opposed to the eJPT, PEH also teaches you some basic skills like Linux commandline and Python Scripting. However, I definitely recommend go play some Hack The Box or TryHackMe after watching the video to get the hands-on experience supplement to your learning.

Preparing for the Exam
The OSCP, in addition to being a difficult cert, is also going to be a shock to your wallet. The cheapest option costs a whopping $1,749 dollars, and that only gives you one exam-attempt, 90 days access to the labs and learning content. Speaking from personal experience, I had to get a 30-day extension, costing $359, to get through all the learning material and get 30 hashes out from the challenge labs. Also, since this is a highly challenging exam, people online said they would on average take 2 to 3 attempts before passing the exam, and each exam attempt costs $249. In total, you will be looking to spend well over $2,500 for the OSCP. I hope you have a job where the cost can be at least partially reimbursed.
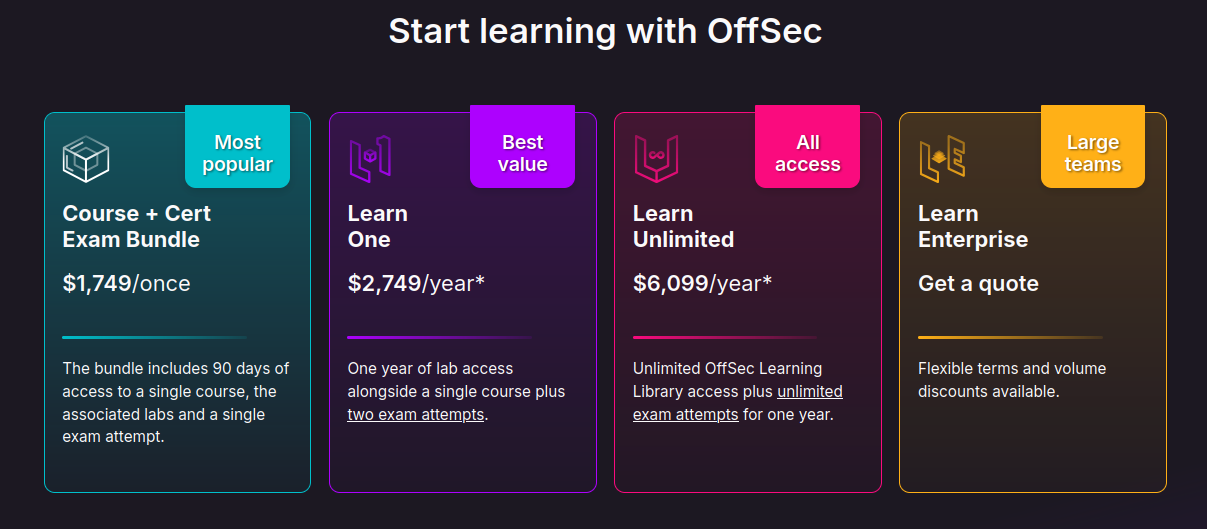
People have also complained that the study material alone doesn’t do a good job at preparing students for the exam. I personally find the study material to be lacking as well, and I had to resort to additional practice. However, there is something about penetration testing that no amount of study material can convey. You must obtain that rational persistence I mentioned above. You must be able to realize which are real vulnerabilities worth pursuing versus rabbit holes that will waste your valuable time, and that can only be obtained through experience and practice. Plus, in real world pentesting, it’s very likely that you will come across technology you are not at all familiar with. You should do your research and find all resources that helps you understand what’s going on. Pentesting is often like swimming in a cold lake in the dark. You have to keep going and find the direction to the shore with only your intuition.
To effectively finish the study material, I suggest set aside 2 to 3 hours per day at a fixed time slot to study for the exam, that way you can exploit your circadian rhythm to achieve the best learning effect, and always to make sure to do the module labs right after you finish reading a learning module. After going through all the learning material, you should work on the challenge labs, which are large networks of vulnerable machines that are meant to be capstones for the entire course. Three of the the challenges labs are full-on mock exams that you should prioritize getting through first. If you got stuck and really can’t find a way to complete the lab, you should seek help in the Offsec discord, but definitely make sure to replicate the solution you found in the lab to commit it to your memory.
Many find it necessary to get additional practice to pass the exam. I found TJ Null’s practice list to be quite helpful (link). In particular, I found the Offsec Proving Ground Practice boxes to be quite similar to the exam format, and I highly recommend completing as many of them as possible before moving onto boxes for other platforms.
Failing the Exam
When it comes to the OSCP, failure is perhaps inevitable for the vast majority of the exam takers. I’ll recount my first exam attempt and hopefully it can be helpful to all those reading. However, do note that my first attempt of the OSCP is that of an older version where the AD portion yields you all 40 points only if you compromise the domain controller.
When I took my first attempt, I failed to get the webcam to work in the proctoring website they require you to keep open during the exam. As a result, I was forced to switch from my main Desktop to my Laptop, which I had less tools set up on. The process of troubleshooting the proctoring website also drained a non-trivial amount of energy out of me, but I nonetheless started my exam attempt an hour late into the exam.
I started by tackling the AD portion. I successfully compromised the first machine, and found my first set of domain credentials. However, I couldn’t find a way to pivot onto the second machine. That led me down a rabbit hole that wasted me a bunch of time without yielding any useful result. I was quite exhausted then, therefore, I made the mistake of start trying out some of the standalone machines instead of taking a break to step away from the exam. Not surprisingly, I wasn’t able to make much progress before the night. I went to bed with only 10 points in my pocket.
When I woke up, I decided that I was going to reset the AD network and redo a port scan on the second machine. And guess what? A port that wasn’t open appeared as open in my nmap scan, which allowed me to login to the second machine with my obtained Domain credential! I was quite displeased about the ordeal, but the exam didn’t care and I couldn’t get any more points before the exam ended.
Since I didn’t have enough points, I didn’t even bother writing the report. I nonetheless felt quite defeated about the failure. Over the course of several months, I began working harder at honing in my pentesting skills by completing more boxes on TJ null’s list. I was then ready for a second attempt.
Passing the Exam
My second attempt began in 7:00 AM in the morning. I had a pretty decent night of sleep before. Learning from my mistake last time, I know the exact set up I need to have the proctoring website working on my desktop. I promptly began my exam and managed to fully compromise the AD network in 3 hours. After taking a break for a light breakfast I spent another 2 hours fully rooting one standalone machine. This means I was merely 10 points away from passing the exam. I was quite excited for the prospect, and thus took another break before coming back. Then, I was stuck and couldn’t make any progress on any of the two remaining machines. Learned from experience, I knew that my mind was a mess and I had to take a break. Therefore, I took an hour-long break to walk out to the gas station outside my apartment and bought two cans of white Monster and sat in the study room in my apartment building for a bit before. After cracking open my drink, and going through everything I did, I finally found something I missed and didn’t investigate, Upon which, I successfully gained initial foothold to the second standalone machine.
The picture below is quite an accurate representation of how I felt at the time:
 I managed to complete the Privilege Escalation portion for that box before calling a stop. With 80 points under my belt, I re-exploited all machines twice and made sure the notes I took are detailed enough to replicate the attack process by merely copy & pasting from it, and all necessary screenshots are taken.
I managed to complete the Privilege Escalation portion for that box before calling a stop. With 80 points under my belt, I re-exploited all machines twice and made sure the notes I took are detailed enough to replicate the attack process by merely copy & pasting from it, and all necessary screenshots are taken.
The report writing also took me longer than I expected. I had some troubles with offsec’s official ODT template, which would always make my Libreoffice freeze for some reason. I personally used this reporting template (link) for my exam report, which allows you to use your favorite editor to write the report in Markdown and convert it to a PDF file. After including all commands and screenshots that formed my attack narrative, the report is nearly 60 pages long. After double-triple checking the report, not wanting to fail the exam because of it, I submitted the report.
After a weekend of anxious waiting, I received the news from Offsec that I finally passed the exam. At the time, I felt like I didn’t really deserve this certification. But as they say, God doesn’t choose the qualified, he qualifies the chosen.
Word of advice
Nowadays, there are arguably cheaper and just-as-practical certifications like TCM’s PNPT or eCPPT comparing to the OSCP, but one still may opt for it due to its industry recognition as the first hands-on penetration testing certification. However, if you do decide to take it, here are all the advices I have for you.
- Make Sure you use a reliable browser that works with the proctoring software! And make sure the correct webcam is selected so that the proctor can see you.
- If something about the exam machine doesn’t feel right, i.e. you don’t see a way into a certain machine, make sure to give the machine a couple of resets. A service might not get set up correctly on the first exam environment launch
- Don’t change machines way too often. Context switches are costly for computer CPUs, and so it is for your brain:)
- Take breaks! At most work 2 to 3 hours at a time, then go outside and touch grass. When you lock-in for an extended period of time, it’s more likely to miss the big picture of what’s actually going on. Take a break immediately if you are stuck. It’s likely your brain is very tired when that happens.
- Get consistent practice before the exam. Even if you feel like you can’t solve a box without looking at other’s write-ups, you are still learning by replicating the steps.
- Practice taking notes and screenshots during practice. That way you can form a good workflow during the exam.
- Turn your practice notes into write-ups if you have the chance. Not only would that help you practice report writing, it also allows you to showcase your progress to potential employers in the future.
Lastly, remember that what is the most important is not to get a ceritification to put on your resume, but to learn knowledge and develop your skills. These days, employers cares less about your degrees and certifications. They want to see your skills and how you make use of them. Git good is more important than having a bunch of certs.
With that, I wish those of you attempting the OSCP good luck, and remember to try harder!